 Program
Control
Program
Control  Program
Control
Program
Control Program control protects you from Trojan horses and other hacker malware by making sure only programs with your permission can access the Internet.
Everything you do on the Internet—from browsing Web pages to downloading MP3 files—is managed by specific applications (programs) on your computer.
Hackers exploit this fact by planting "malware"—literally, evil programs—on your computer. Sometimes they send out malware as e-mail attachments with innocent names like "screensaver.exe." If you open the attachment, you install the malware on you computer without even knowing it. Other times, they convince you to download the malware from a server by making it masquerade as an update to a legitimate program.
Once on your machine, malware can wreak havoc in a variety of ways. It can raid your address book and send itself to everyone in it, or it can listen for connection requests from the Internet. The hacker who distributed the malware can then contact it and give it instructions, effectively taking control of your computer.
ZoneAlarm Pro's program control features use the following methods to protect you from malware attacks:
Whenever a program on your computer wants to access the Internet, ZoneAlarm Pro authenticates it via its MD5 signature.
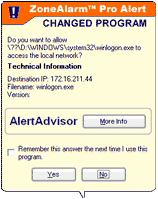 If
the program has been altered since the last time it accessed the Internet, ZoneAlarm
Pro displays a Changed Program alert (shown at left). YOU decide whether the
program should be allowed access or not.
If
the program has been altered since the last time it accessed the Internet, ZoneAlarm
Pro displays a Changed Program alert (shown at left). YOU decide whether the
program should be allowed access or not.
For added security, ZoneAlarm Pro also authenticates the components (for example, DLL files) associated with the program's main executable file. If a component has been altered, you'll see a Program Component alert similar in appearance to a Changed Program alert.
For more information about program authentication or about alerts, see Related Topics.
When you're using ZoneAlarm Pro, no program on your computer can access the Internet or your local network, or act as a server, unless you give it permission to do so.

A New Program alert (shown at left) asks you if you want to grant the program access permission. If you're not sure whether to click Yes or No, you can click the More Info to have Zone Labs' Alert Advisor help you decide what to do. A Program Component alert (similar to a new program alert) lets you know if the program is using a component that is new or has changed. |
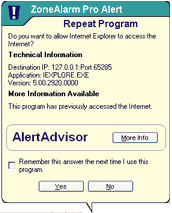
A Repeat Program alert (shown at left) asks you if you want to grant (or deny) access permission to a program that has requested it before.
|
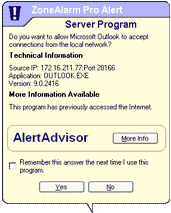
A Server Program alert (shown at left) asks you if you want grant server permission to a program.
|
Advanced Program Control informs you when one program tries to use another program to gain access to the Internet.
When a program tries to use another program to gain network access...
An Advanced Program alert asks you if you want to grant the program permission to access through other programs.
Program authentication
ZoneAlarm Pro alerts
Trojan horse
A malicious program that masquerades as something useful or harmless, such as
a screen saver. Some Trojan horses operate by setting themselves up as servers
on your computer, listening for connections from the outside. If a hacker succeeds
in contacting the program, he can effectively take control of your computer.
This is why it's important to only give server permission to programs you know
and trust. Other Trojan horses attempt to contact a remote address automatically.
access permission
Access permission allows a program on your computer to initiate communications
with another computer. This is distinct from server permission, which allows
a program to "listen" for connection requests from other computers.
You can give a program access permission for the Trusted Zone, the Internet
Zone, or both.
Several common applications may need access permission to operate normally. For example, your browser needs access permission in order to contact your ISP's servers. Your e-mail client (for example, MS Outlook) needs access permission in order to send or receive e-mail.
The following basic options are available for each program:
Allow
the program to connect to computers in the Internet Zone / Trusted Zone
Block the program from accessing computers in the Internet Zone / Trusted
Zone
Ask whether the program should have access permission (show Repeat
Program alert)
server permission
Server permission allows a program on your computer to "listen" for
connection requests from other computers, in effect giving those computers the
power to initiate communications with yours. This is distinct from access permission,
which allows a program to initiate a communications session with another computer.
Several common types of applications, such as chat programs, e-mail clients, and Internet Call Waiting programs, may need server permission to operate properly. Grant server permission only to programs you're sure you trust, and that require it in order to work.
If possible, avoid granting a program server permission for the Internet Zone. If you need to accept incoming connections from only a small number of machines, add those machines to the Trusted Zone, and then allow the program server permission for the Trusted Zone only.
The following basic options are available for each program
Allow
the program to listen for connection requests
Block the program from listening for connection requests
Ask me whether to allow the program to listen for connection requests
(show Server Program alert)
component
A small program or set of functions that larger programs call on to perform
specific tasks. Some components may be used by several different programs simultaneously.
Windows operating systems provide many component DLLs (Dynamic Link Libraries)
for use by a variety of Windows applications.
MD5 signature
A digital "fingerprint" used to verify the integrity of a file. If
a file has been changed in any way (for example, if a program has been compromised
by a hacker), its MD5 signature will change as well.